Create Policy and Role
Create Role
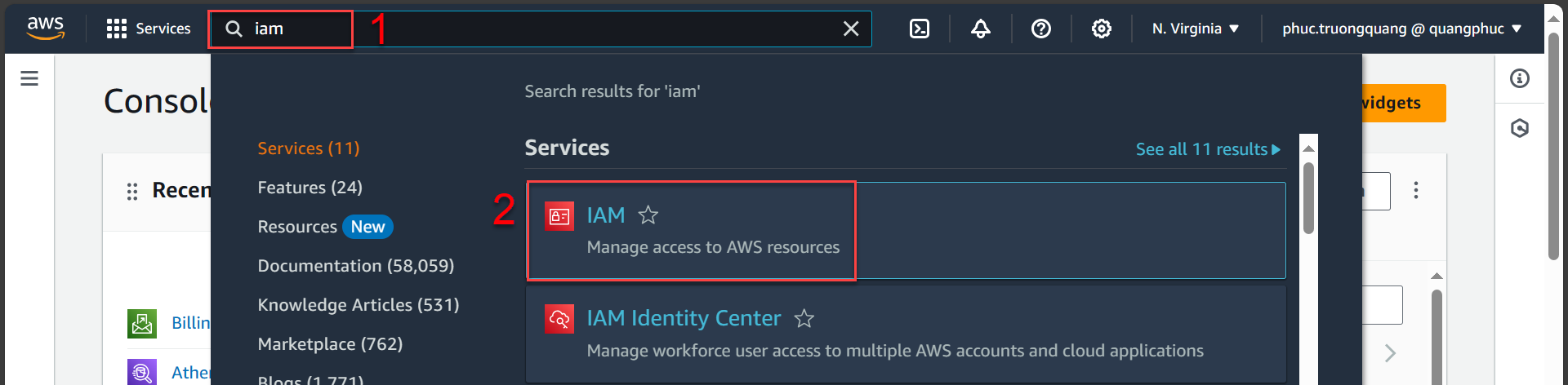
Access AWS Management Console
- Search IAM
- Select IAM
In the interface IAM
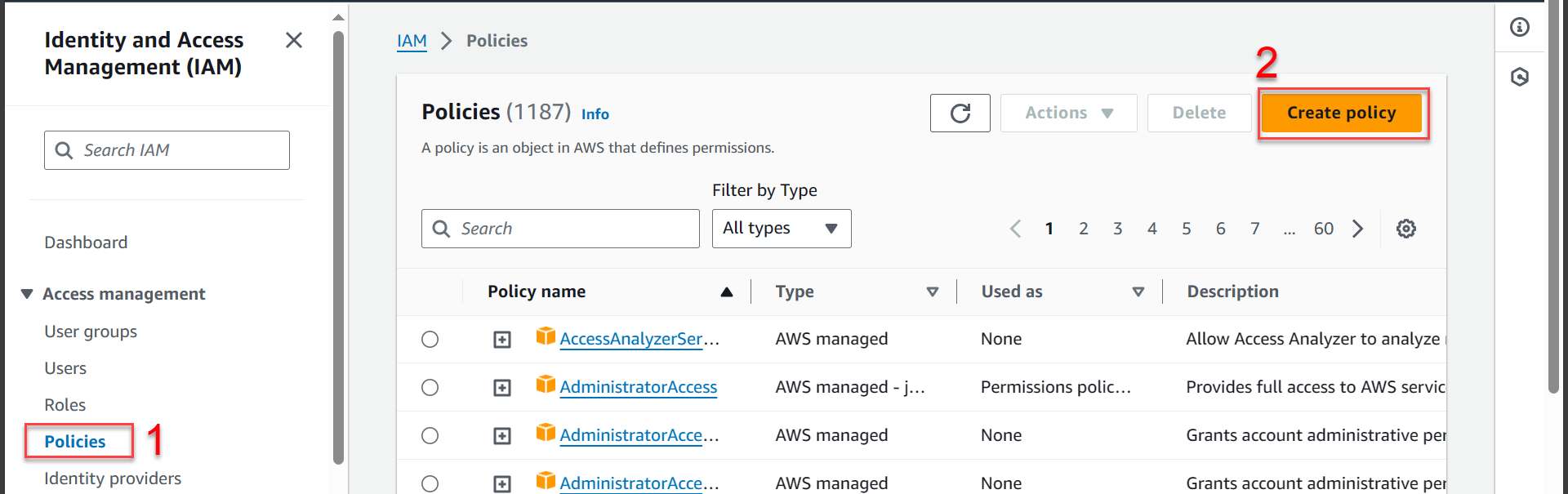
- Select Policies
- Select Create policy
In the interface Specify permissions
- Select JSON delete the old code and copy the new code below
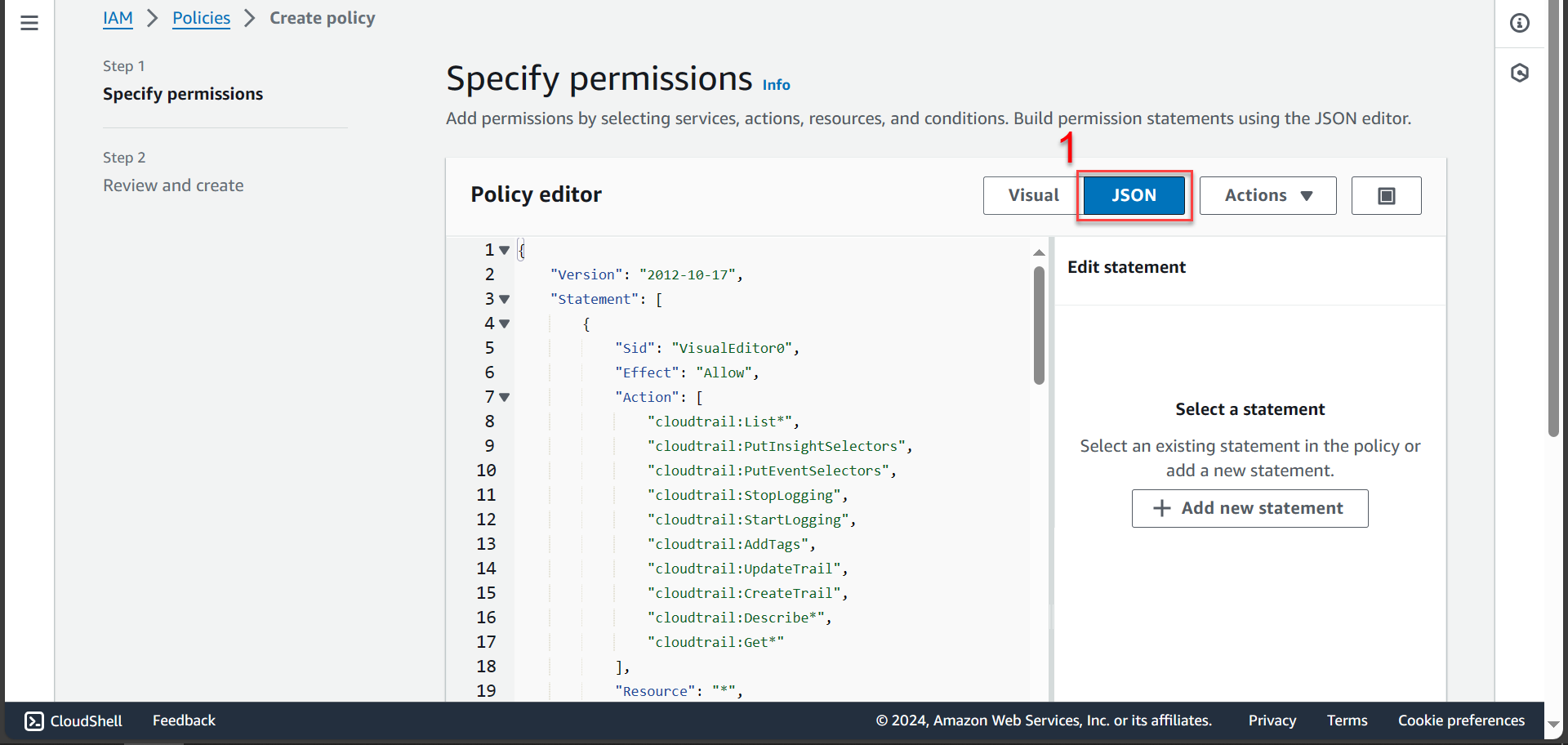
This policy will grant permissions to each function in this lab. You can customize the permissions in this policy. This code is delegating authority to Region US East (Virginia), so this part will be “aws:RequestedRegion”: “us-east-1” (If you are in another Region, you should edit each “aws:RequestedRegion”)
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"cloudtrail:List*",
"cloudtrail:PutInsightSelectors",
"cloudtrail:PutEventSelectors",
"cloudtrail:StopLogging",
"cloudtrail:StartLogging",
"cloudtrail:AddTags",
"cloudtrail:UpdateTrail",
"cloudtrail:CreateTrail",
"cloudtrail:Describe*",
"cloudtrail:Get*"
],
"Resource": "*",
"Condition": {
"ForAllValues:StringEquals": {
"aws:RequestedRegion": "us-east-1"
}
}
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"cloudwatch:List*",
"cloudwatch:Get*",
"cloudwatch:Describe*"
],
"Resource": "*",
"Condition": {
"ForAllValues:StringEquals": {
"aws:RequestedRegion": "us-east-1"
}
}
},
{
"Sid": "VisualEditor2",
"Effect": "Allow",
"Action": [
"config:Get*",
"config:List*",
"config:Describe*"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestedRegion": "us-east-1"
}
}
},
{
"Sid": "VisualEditor3",
"Effect": "Allow",
"Action": [
"iam:Get*",
"iam:List*",
"iam:AttachRolePolicy"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestedRegion": "us-east-1"
}
}
},
{
"Sid": "VisualEditor4",
"Effect": "Allow",
"Action": [
"kms:EnableKeyRotation",
"kms:EnableKey",
"kms:Decrypt",
"kms:TagResource",
"kms:UntagResource",
"kms:List*",
"kms:Encrypt",
"kms:Get*",
"kms:CreateAlias",
"kms:Describe*",
"kms:CreateKey",
"kms:DisableKey"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestedRegion": "us-east-1"
}
}
},
{
"Sid": "VisualEditor5",
"Effect": "Allow",
"Action": [
"organizations:Describe*",
"organizations:List*"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestedRegion": "us-east-1"
}
}
},
{
"Sid": "VisualEditor6",
"Effect": "Allow",
"Action": [
"s3:PutAccountPublicAccessBlock",
"s3:PutBucketPublicAccessBlock",
"s3:PutBucketOwnershipControls",
"s3:Get*",
"s3:CreateBucket",
"s3:List*",
"s3:PutObject",
"s3:PutObjectVersionAcl",
"s3:PutBucketAcl",
"s3:PutBucketPolicy",
"s3:PutAccessPointPolicy",
"s3:PutBucketVersioning",
"s3:PutObjectAcl",
"iam:PassRole",
"iam:CreateServiceLinkedRole"
],
"Resource": "*"
},
{
"Sid": "VisualEditor7",
"Effect": "Allow",
"Action": "tag:Get*",
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestedRegion": "us-east-1"
}
}
},
{
"Sid": "VisualEditor8",
"Effect": "Deny",
"Action": "s3:*",
"Resource": "*",
"Condition": {
"ForAllValues:StringNotEqualsIfExists": {
"aws:RequestedRegion": "us-east-1"
}
}
}
]
}
- After completing the above step, we scroll down to the bottom of the page and click Next
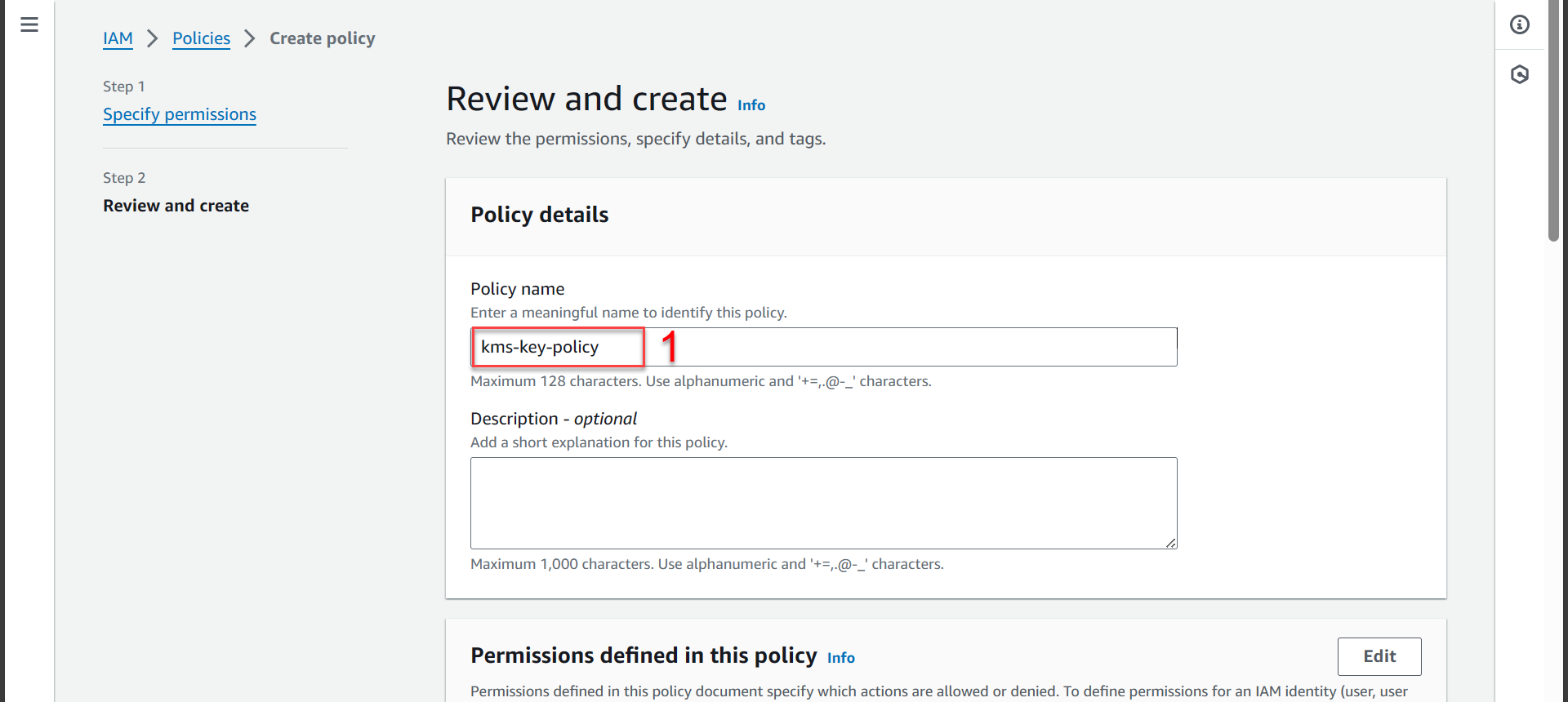
- In section Review and create
You can name it differently as you like!
- Policy name import
kms-key-policy
- After entering the Policy name, scroll down to the bottom of the page and click Create policy
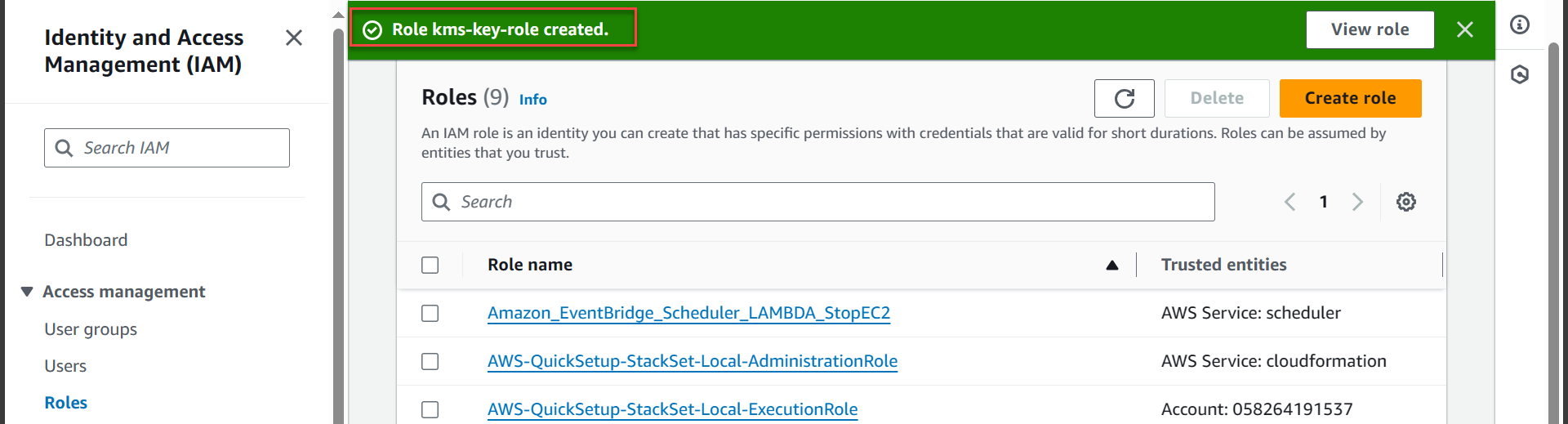
- Notice of successful creation of Policy
Next step we will create Role
In the interface IAM
- Select Roles
- Select Create role
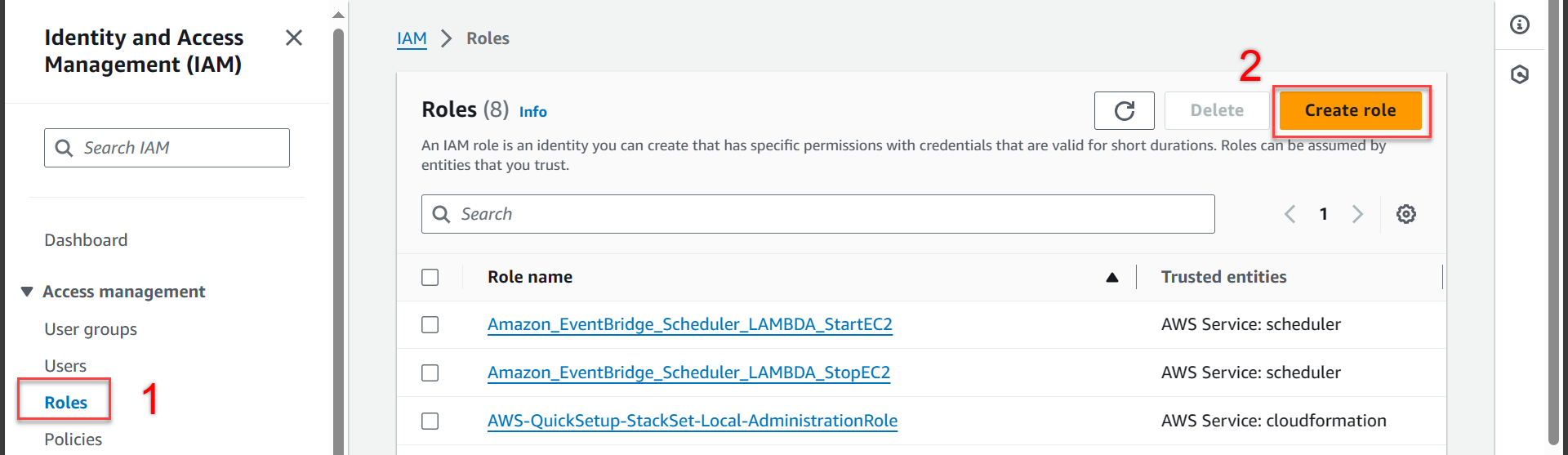
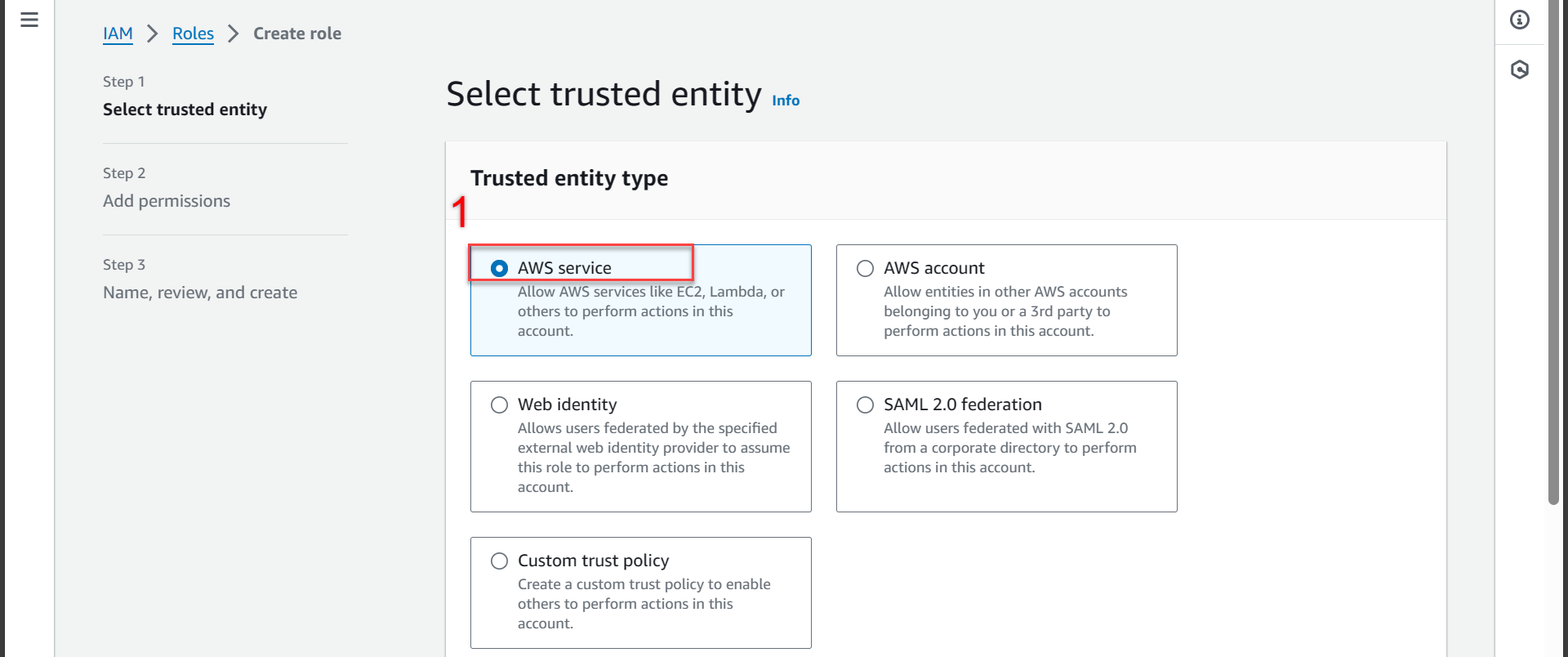
In section Select trusted entity
- Select AWS service
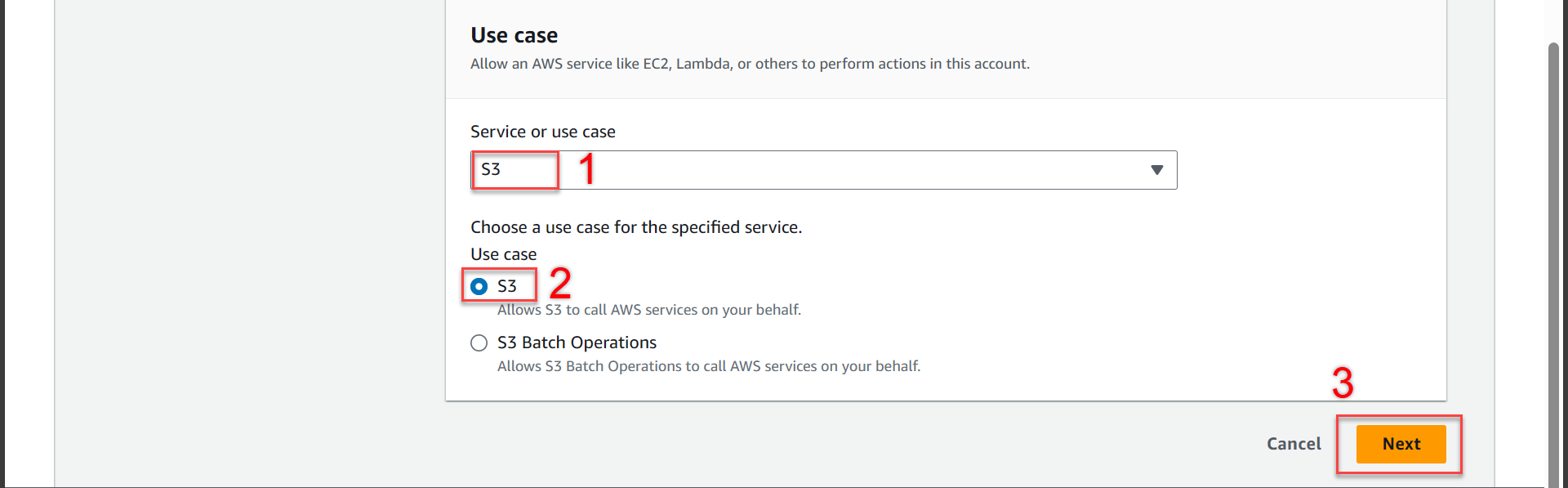
- Scroll down to the section Use case
- In the Service or use case section, select S3
- In the Use case section, select S3
- And press Next
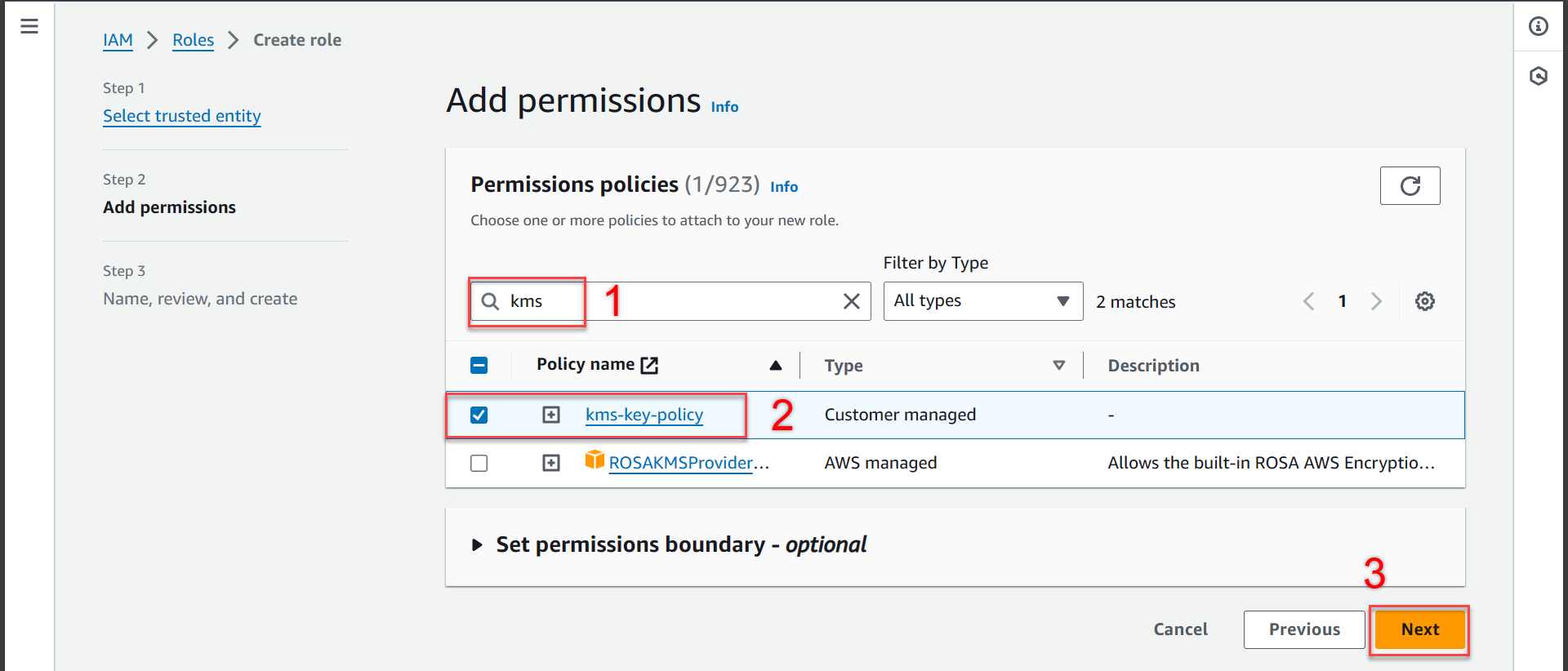
- In the Add permissions section
- Select the search bar and search for the newly created kms policy
- Select the policy you just created
- Click Next
- In the Name, review, and create section
You can name it differently as you like!
- Role name import
kms-key-role
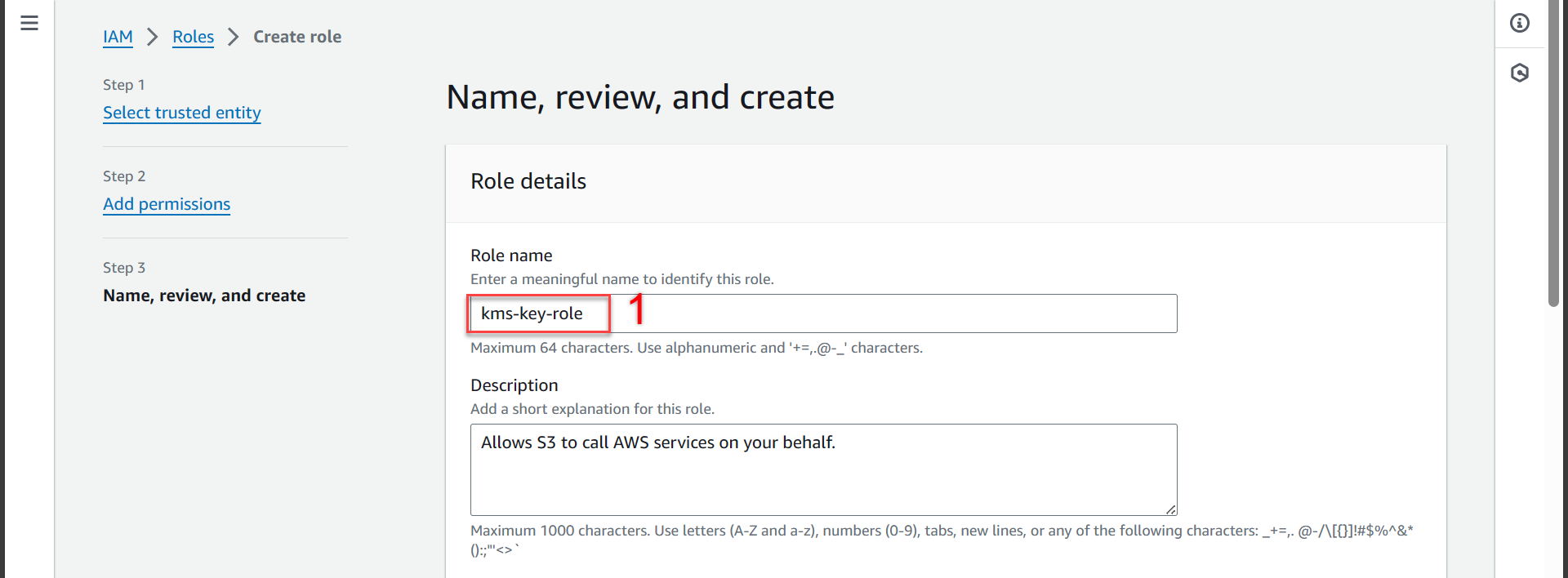
- Scroll down and press Create role

- Notice of successful role creation